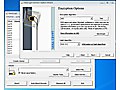
 VeraCrypt is a full-disk encryption software derived from TrueCrypt. It revises some of the algorithm usage against brute-force attacks. For example system partitions use use larger rounds of PBKDF2 key stretching. The partition and container format is different to that of TrueCrypt however.
VeraCrypt is a full-disk encryption software derived from TrueCrypt. It revises some of the algorithm usage against brute-force attacks. For example system partitions use use larger rounds of PBKDF2 key stretching. The partition and container format is different to that of TrueCrypt however.
 Duplicati is a free, open source, backup client that securely stores encrypted, incremental, compressed backups on cloud storage services and remote file servers. It works with: Amazon S3, IDrive e2, Backblaze (B2), Box, Dropbox, FTP, Google Cloud and Drive, MEGA, Microsoft Azure and OneDrive, Rackspace Cloud Files, OpenStack Storage (Swift), Sia, Storj DCS, SSH (SFTP), WebDAV, Tencent Cloud Object Storage (COS), and more!
Duplicati is a free, open source, backup client that securely stores encrypted, incremental, compressed backups on cloud storage services and remote file servers. It works with: Amazon S3, IDrive e2, Backblaze (B2), Box, Dropbox, FTP, Google Cloud and Drive, MEGA, Microsoft Azure and OneDrive, Rackspace Cloud Files, OpenStack Storage (Swift), Sia, Storj DCS, SSH (SFTP), WebDAV, Tencent Cloud Object Storage (COS), and more!
 croc is a tool that allows any two computers to simply and securely transfer files and folders. AFAIK, croc is the only CLI file-transfer tool that does all of the following: allows any two computers to transfer data (using a relay) provides end-to-end encryption (using PAKE) enables easy cross-platform transfers (Windows, Linux, Mac) allows multiple file transfers allows resuming transfers that are interrupted local server or port-forwarding not needed ipv6-first wi
croc is a tool that allows any two computers to simply and securely transfer files and folders. AFAIK, croc is the only CLI file-transfer tool that does all of the following: allows any two computers to transfer data (using a relay) provides end-to-end encryption (using PAKE) enables easy cross-platform transfers (Windows, Linux, Mac) allows multiple file transfers allows resuming transfers that are interrupted local server or port-forwarding not needed ipv6-first wi
 Encrypted address book to manage contacts in a privacy-focused way. With cloud connectivity to Nextcloud and some other cloud providers.
Encrypted address book to manage contacts in a privacy-focused way. With cloud connectivity to Nextcloud and some other cloud providers.
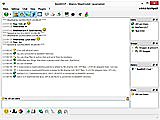 BeeBEEP is a secure networking chat. It allows simple chat-style instant messaging, group chats, friend lists, and exchanging files. It works in any intranet environment, or through public networks.
BeeBEEP is a secure networking chat. It allows simple chat-style instant messaging, group chats, friend lists, and exchanging files. It works in any intranet environment, or through public networks.
 gofoss.net is the ultimate, free and open source guide to online privacy, data ownership and durable tech. Our aim is to make privacy respecting, free and open source software accessible to all. Learn how to: safely browse the Internet; keep your conversations private; protect your data; unlock your computer's full potential; stay mobile and free; own your cloud; avoid filter bubbles, surveillance & censorship.
gofoss.net is the ultimate, free and open source guide to online privacy, data ownership and durable tech. Our aim is to make privacy respecting, free and open source software accessible to all. Learn how to: safely browse the Internet; keep your conversations private; protect your data; unlock your computer's full potential; stay mobile and free; own your cloud; avoid filter bubbles, surveillance & censorship.
 Photok is a free Photo-Safe. It stores your photos encrypted on your device and hides them from others. It uses technologies like, AES-256 encryption standard or bcrypt, to keep your photos secure. Photok is completely free, open source, and contains no ads.
Photok is a free Photo-Safe. It stores your photos encrypted on your device and hides them from others. It uses technologies like, AES-256 encryption standard or bcrypt, to keep your photos secure. Photok is completely free, open source, and contains no ads.
 Duplicity is a bandwidth-efficient backup system with built-in encryption. It produces incremental tar volumes and stores them onto local or remote servers using librsync. It utilizes GnuPG for encryption and signing.
Duplicity is a bandwidth-efficient backup system with built-in encryption. It produces incremental tar volumes and stores them onto local or remote servers using librsync. It utilizes GnuPG for encryption and signing.
 An extension for caja which allows encryption and decryption of OpenPGP files using GnuPG. Ported to Caja from seahorse-nautilus.
An extension for caja which allows encryption and decryption of OpenPGP files using GnuPG. Ported to Caja from seahorse-nautilus.
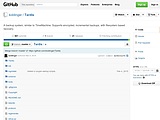 Tardis is a backup system similar to TimeMachine which allows encrypted and incremental backups, with filesystem-based recovery. It's based on a client and server architecture, and provides a FUSE driver and VCS-like revision archive access.
Tardis is a backup system similar to TimeMachine which allows encrypted and incremental backups, with filesystem-based recovery. It's based on a client and server architecture, and provides a FUSE driver and VCS-like revision archive access.
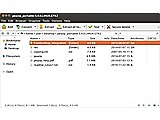 PeaZip is a cross-platform compression and archiving tool. It utilizes code from 7-Zip, Pea, FreeARC, PAQ, QUAD and UPX. Besides having full 7z, lzma, xzip, gzip, bzip2 and standard ZIP and TAR support, it can also read from APK, ZIPX, ARJ, CAB, CPIO, LZO, RAR, ISO, JAR, XAR, ACE, ARC, and various application or file system containers. AES256 encryption is further supported in some archive types, or splitting and merging, converting between formats, or secure archive content deletion, and creati
PeaZip is a cross-platform compression and archiving tool. It utilizes code from 7-Zip, Pea, FreeARC, PAQ, QUAD and UPX. Besides having full 7z, lzma, xzip, gzip, bzip2 and standard ZIP and TAR support, it can also read from APK, ZIPX, ARJ, CAB, CPIO, LZO, RAR, ISO, JAR, XAR, ACE, ARC, and various application or file system containers. AES256 encryption is further supported in some archive types, or splitting and merging, converting between formats, or secure archive content deletion, and creati
 Cryptsetup is a convenience wrapper to set up disk encryption using the dm-crypt kernel module. It supports raw volumes, LUKS partitions, loop-AES and TrueCrypt containers.
Cryptsetup is a convenience wrapper to set up disk encryption using the dm-crypt kernel module. It supports raw volumes, LUKS partitions, loop-AES and TrueCrypt containers.
 Naamari is AES&SHA-based crypto-synchronizer for cloud/remote file storage, with cryptographic and transport modules being separate applications. It works with 4 locations. 1st: local dir with original files. 2nd: dir containing folder structure and names of files placed into storage (but not content). 3rd & 4th - storages: local (another local dir) and remote (say, a cloud). In storages, there are no folders, files have pseudo-random names and encrypted content ("flattening"). The main module
Naamari is AES&SHA-based crypto-synchronizer for cloud/remote file storage, with cryptographic and transport modules being separate applications. It works with 4 locations. 1st: local dir with original files. 2nd: dir containing folder structure and names of files placed into storage (but not content). 3rd & 4th - storages: local (another local dir) and remote (say, a cloud). In storages, there are no folders, files have pseudo-random names and encrypted content ("flattening"). The main module
 gpgpwd is a terminal-based password manager. It stores a list of passwords and their associated usernames in a GnuPG-encrypted file, and allows you to easily retrieve, change, and add to that file as needed. It also generates random passwords which you can use, easily allowing you to have one "master password" (for your gpg key), with one unique and random password for each website or service you use, ensuring that your other accounts stay safe even if one password gets leaked. gpgpwd can als
gpgpwd is a terminal-based password manager. It stores a list of passwords and their associated usernames in a GnuPG-encrypted file, and allows you to easily retrieve, change, and add to that file as needed. It also generates random passwords which you can use, easily allowing you to have one "master password" (for your gpg key), with one unique and random password for each website or service you use, ensuring that your other accounts stay safe even if one password gets leaked. gpgpwd can als
 TCHunt-ng attempts to reveal encrypted files stored on a filesystem. The program is successful in finding TrueCrypt/VeraCrypt containers, EncFS encrypted files, PGP/GPG messages (and keys), and other files made up of random data. The code is based on ideas laid out in the project of Stephen Judge named TCHunt, hence the name.
TCHunt-ng attempts to reveal encrypted files stored on a filesystem. The program is successful in finding TrueCrypt/VeraCrypt containers, EncFS encrypted files, PGP/GPG messages (and keys), and other files made up of random data. The code is based on ideas laid out in the project of Stephen Judge named TCHunt, hence the name.
 Ricochet is a peer-to-peer, anonymous and secure instant messaging system utilizing Tor. It allows chatting with anyone without exposing an identity or IP address. It does not reveal any meta data, contacts, as it does not rely on central servers.
Ricochet is a peer-to-peer, anonymous and secure instant messaging system utilizing Tor. It allows chatting with anyone without exposing an identity or IP address. It does not reveal any meta data, contacts, as it does not rely on central servers.
 Fort integrates itself into the Windows file explorer. This allows you to easily encrypt (and decrypt) files via the Explorer context menu and to protect them with a password. All file types are supported. Fort can be also used to encrypt files in Onedrive, Dropbox and other similar services. Fort takes security seriously and uses AES with 256bit keys. On decryption Fort checks that the data is not tampered in any way and informs if data tampering is detected. For each file, Fort generates a ra
Fort integrates itself into the Windows file explorer. This allows you to easily encrypt (and decrypt) files via the Explorer context menu and to protect them with a password. All file types are supported. Fort can be also used to encrypt files in Onedrive, Dropbox and other similar services. Fort takes security seriously and uses AES with 256bit keys. On decryption Fort checks that the data is not tampered in any way and informs if data tampering is detected. For each file, Fort generates a ra
 The RedMatrix (aka "red") is an open source webapp providing a complete decentralised publishing, sharing, and communications system. It combines communications (private messaging, chat and social networking), and media management (photos, events, files, web pages, shareable apps) with enough features to make your head spin. What makes the RedMatrix unique is what we call "magic authentication" - which is based on our groundbreaking work in decentralised identity services. This ties all RedMa
The RedMatrix (aka "red") is an open source webapp providing a complete decentralised publishing, sharing, and communications system. It combines communications (private messaging, chat and social networking), and media management (photos, events, files, web pages, shareable apps) with enough features to make your head spin. What makes the RedMatrix unique is what we call "magic authentication" - which is based on our groundbreaking work in decentralised identity services. This ties all RedMa
 A pure C library for asymmetric cryptography algorithm.Include Modified-Rabin signature scheme,Rabin encryption scheme,H. C. Williams encryption scheme.
A pure C library for asymmetric cryptography algorithm.Include Modified-Rabin signature scheme,Rabin encryption scheme,H. C. Williams encryption scheme.
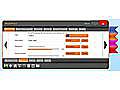 MakiPass is a desktop tool for encrypting files. It utilizes the AES cipher, provides high-entropy password generation, capture keyloggers per keystroke simulation, allows process introspection. It can also be used as simple backup manager, can export data as JSON or ZIP file, and comes with a simple text note / editor facility.
MakiPass is a desktop tool for encrypting files. It utilizes the AES cipher, provides high-entropy password generation, capture keyloggers per keystroke simulation, allows process introspection. It can also be used as simple backup manager, can export data as JSON or ZIP file, and comes with a simple text note / editor facility.
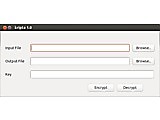 kripta is a small tool to encrypt files using Tiny Encryption Algorithm (TEA) with user-defined keys of 4-16 characters. It's a command line tool, but also comes with a small Gnome or Windows GUI.
kripta is a small tool to encrypt files using Tiny Encryption Algorithm (TEA) with user-defined keys of 4-16 characters. It's a command line tool, but also comes with a small Gnome or Windows GUI.
 Pretty Good Privacy is already there. With GnuPG we have a great implementation. But the handling is too complicated for many people. They don't understand. That's the reason for pEp – pretty Easy privacy. It automates the usage of GnuPG, it automates keymanagement, it encrypts whenever possible while the user just presses “send”. And it's not only (but also) for E-Mail. It's for Whatsapp, Facebook messages, Jabber, and many more. And the best: when both sides are using a client with the p
Pretty Good Privacy is already there. With GnuPG we have a great implementation. But the handling is too complicated for many people. They don't understand. That's the reason for pEp – pretty Easy privacy. It automates the usage of GnuPG, it automates keymanagement, it encrypts whenever possible while the user just presses “send”. And it's not only (but also) for E-Mail. It's for Whatsapp, Facebook messages, Jabber, and many more. And the best: when both sides are using a client with the p
 PHPSecLib is a pure PHP userland collection of encryption functions. It comes with an arbitrary-precision integer arithmetic library, and PKCS#1 compliant RSA, DES, 3DES, RC4, Rijndael, AES, Blowfish, Twofish, and implementations of SSH-1, SSH-2, SFTP, and X.509.
PHPSecLib is a pure PHP userland collection of encryption functions. It comes with an arbitrary-precision integer arithmetic library, and PKCS#1 compliant RSA, DES, 3DES, RC4, Rijndael, AES, Blowfish, Twofish, and implementations of SSH-1, SSH-2, SFTP, and X.509.
 LUKSUS is a text-based program for Linux and BSD which runs in a terminal window or console. LUKSUS lets you encrypt your files, hardrives, usb sticks and virtual container using your operating system's internal encryption mechanism and acts as the frontend to the internal encryption mechanism. It can use the following encryption facilities: LUKS, Truecrypt, GELI and GNUPGP. It works on Linux, DragonflyBSD and FreeBSD. LUKSUS can also encrypt single files with GNU Privacy Guard or OpenSSL. Thi
LUKSUS is a text-based program for Linux and BSD which runs in a terminal window or console. LUKSUS lets you encrypt your files, hardrives, usb sticks and virtual container using your operating system's internal encryption mechanism and acts as the frontend to the internal encryption mechanism. It can use the following encryption facilities: LUKS, Truecrypt, GELI and GNUPGP. It works on Linux, DragonflyBSD and FreeBSD. LUKSUS can also encrypt single files with GNU Privacy Guard or OpenSSL. Thi
|