 pimhasher is a program inspired by VeraCrypt's PIM (Personal Iterations Multiplier) feature, designed to provide the same functionality for LUKS (Linux Unified Key Setup)
pimhasher is a program inspired by VeraCrypt's PIM (Personal Iterations Multiplier) feature, designed to provide the same functionality for LUKS (Linux Unified Key Setup)
 Open-Source Cryptographic APIs Bouncy Castle was designed for developers by developers. Bouncy Castle offers open-source code with well-trodden paths of implementation throughout its supporting APIs. Being able to work with cryptography and secure protocols such as CMS, S/MIME, PGP, and TLS are fundamental to today’s connected applications and business processes. Bouncy Castle provides APIs which help reduce the effort and complexity behind implementing and maintaining security services, helpin
Open-Source Cryptographic APIs Bouncy Castle was designed for developers by developers. Bouncy Castle offers open-source code with well-trodden paths of implementation throughout its supporting APIs. Being able to work with cryptography and secure protocols such as CMS, S/MIME, PGP, and TLS are fundamental to today’s connected applications and business processes. Bouncy Castle provides APIs which help reduce the effort and complexity behind implementing and maintaining security services, helpin
 LibreSSL Portable is a free version of the SSL/TLS protocol forked from OpenSSL, and developed by the OpenBSD project. LibreSSL is developed as part of the OpenBSD system, with lots of ancient cruft and security woes already fixed. The portable version for other Unices is developed alongside.
LibreSSL Portable is a free version of the SSL/TLS protocol forked from OpenSSL, and developed by the OpenBSD project. LibreSSL is developed as part of the OpenBSD system, with lots of ancient cruft and security woes already fixed. The portable version for other Unices is developed alongside.
 The Mandos system allows computers to have encrypted root file systems and at the same time be capable of remote or unattended reboots. The computers run a small client program in the initial RAM disk environment which will communicate with a server over a network. All network communication is encrypted using TLS. The clients are identified by the server using a TLS key that is unique to each client. The server sends the clients an encrypted password. The encrypted password is decrypted by the c
The Mandos system allows computers to have encrypted root file systems and at the same time be capable of remote or unattended reboots. The computers run a small client program in the initial RAM disk environment which will communicate with a server over a network. All network communication is encrypted using TLS. The clients are identified by the server using a TLS key that is unique to each client. The server sends the clients an encrypted password. The encrypted password is decrypted by the c
 OpenSSH is a BSD/Linux implementation of SSH1 and SSH2 for encrypted terminal connections, tunneling and file transfers. It includes the sshd server, scp and sftp, and various utility tools such as ssh-add, ssh-agent, ssh-keysign, ssh-keyscan, ssh-keygen, and the sftp-server.
OpenSSH is a BSD/Linux implementation of SSH1 and SSH2 for encrypted terminal connections, tunneling and file transfers. It includes the sshd server, scp and sftp, and various utility tools such as ssh-add, ssh-agent, ssh-keysign, ssh-keyscan, ssh-keygen, and the sftp-server.
 Tomb is a system to make strong encryption easy for everyday use. A tomb is like a locked folder that can be safely transported and hidden in a filesystem. Its keys can be kept separate; for example, you can keep the tomb on your computer and its key on a USB stick. Tomb is written in code that is easy to review and links shared components: it consists of a ZShell script and desktop integration apps; it uses standard GNU tools and the crypto API of the Linux kernel (dm-crypt) via cryptsetup.
Tomb is a system to make strong encryption easy for everyday use. A tomb is like a locked folder that can be safely transported and hidden in a filesystem. Its keys can be kept separate; for example, you can keep the tomb on your computer and its key on a USB stick. Tomb is written in code that is easy to review and links shared components: it consists of a ZShell script and desktop integration apps; it uses standard GNU tools and the crypto API of the Linux kernel (dm-crypt) via cryptsetup.
 Calendar Lock PEA displays password encrypted iCalendar compatible calendars in monthly, weekly and daily view with optional cloud connection. The calendars are always encrypted on the device or in the cloud. iCalendars from other applications can be imported.
Calendar Lock PEA displays password encrypted iCalendar compatible calendars in monthly, weekly and daily view with optional cloud connection. The calendars are always encrypted on the device or in the cloud. iCalendars from other applications can be imported.
 The Enrollment over Secure Transport (EST) protocol describes a simple, yet functional, certificate management protocol targeting Public Key Infrastructure (PKI) clients that need to acquire client certificates and associated Certification Authority (CA) certificates. This protocol supports both client-generated public/private key pairs and those generated by the CA. The nginx-http-est module provides EST functionality for a Nginx server.
The Enrollment over Secure Transport (EST) protocol describes a simple, yet functional, certificate management protocol targeting Public Key Infrastructure (PKI) clients that need to acquire client certificates and associated Certification Authority (CA) certificates. This protocol supports both client-generated public/private key pairs and those generated by the CA. The nginx-http-est module provides EST functionality for a Nginx server.
 Trusted QSL keeps eQSL an open and free activity for amateur radio operators. It promotes the Digital Signature Standard (DSS).
Trusted QSL keeps eQSL an open and free activity for amateur radio operators. It promotes the Digital Signature Standard (DSS).
 GnuPG (the GNU Privacy Guard or GPG) is GNU's tool for secure communication and data storage. It can be used to encrypt data and to create digital signatures. It includes an advanced key management facility and is compliant with the proposed OpenPGP Internet standard as described in RFC2440. As such, it is meant to be compatible with PGP from NAI, Inc. Because it does not use any patented algorithms, it can be used without any restrictions.
GnuPG (the GNU Privacy Guard or GPG) is GNU's tool for secure communication and data storage. It can be used to encrypt data and to create digital signatures. It includes an advanced key management facility and is compliant with the proposed OpenPGP Internet standard as described in RFC2440. As such, it is meant to be compatible with PGP from NAI, Inc. Because it does not use any patented algorithms, it can be used without any restrictions.
 Bypassing slowaes web-scraping protection aes.js slowAES.decrypt(c, 2, a, b) algorithym with esp8266 (nodemcu) HttpClient object with __test cookie
Bypassing slowaes web-scraping protection aes.js slowAES.decrypt(c, 2, a, b) algorithym with esp8266 (nodemcu) HttpClient object with __test cookie
 Browser Notebook displays, encrypts and stores notes locally in the Web browser. Unlike similar programs, the texts are stored nowhere else than in your browser and always in encrypted form. The plaintext is kept in memory only. You can either use the online version without any registration or installation, or you can download the offline version and use it without Internet access.
Browser Notebook displays, encrypts and stores notes locally in the Web browser. Unlike similar programs, the texts are stored nowhere else than in your browser and always in encrypted form. The plaintext is kept in memory only. You can either use the online version without any registration or installation, or you can download the offline version and use it without Internet access.
 Image Lock PEA protects photos, drawings, and documents in image format with a password. Thanks to the integrated viewer the images are never stored unencrypted on the hard disk, but are held only in memory. The Image Lock PEA uses functions to derive the key from the password, that protect also against attackers with a high budget. In addition to the confidentiality, an authenticated encryption protects the integrity and authenticity of the images.
Image Lock PEA protects photos, drawings, and documents in image format with a password. Thanks to the integrated viewer the images are never stored unencrypted on the hard disk, but are held only in memory. The Image Lock PEA uses functions to derive the key from the password, that protect also against attackers with a high budget. In addition to the confidentiality, an authenticated encryption protects the integrity and authenticity of the images.
 Notebook PEA protects texts using authenticated encryption (EAX mode) for confidentiality, integrity, and authenticity of the text. Notebook PEA works like a self-decrypting archive (SDA): the plaintext is never stored on disk, instead it is displayed in a simple text editor with some styling functionality, redo/undo and copy, cut, paste commands. Supports access to Nextcloud, Owncloud and other cloud providers that support the WebDAV protocol.
Notebook PEA protects texts using authenticated encryption (EAX mode) for confidentiality, integrity, and authenticity of the text. Notebook PEA works like a self-decrypting archive (SDA): the plaintext is never stored on disk, instead it is displayed in a simple text editor with some styling functionality, redo/undo and copy, cut, paste commands. Supports access to Nextcloud, Owncloud and other cloud providers that support the WebDAV protocol.
 gofoss.net is the ultimate, free and open source guide to online privacy, data ownership and durable tech. Our aim is to make privacy respecting, free and open source software accessible to all. Learn how to: safely browse the Internet; keep your conversations private; protect your data; unlock your computer's full potential; stay mobile and free; own your cloud; avoid filter bubbles, surveillance & censorship.
gofoss.net is the ultimate, free and open source guide to online privacy, data ownership and durable tech. Our aim is to make privacy respecting, free and open source software accessible to all. Learn how to: safely browse the Internet; keep your conversations private; protect your data; unlock your computer's full potential; stay mobile and free; own your cloud; avoid filter bubbles, surveillance & censorship.
 Photok is a free Photo-Safe. It stores your photos encrypted on your device and hides them from others. It uses technologies like, AES-256 encryption standard or bcrypt, to keep your photos secure. Photok is completely free, open source, and contains no ads.
Photok is a free Photo-Safe. It stores your photos encrypted on your device and hides them from others. It uses technologies like, AES-256 encryption standard or bcrypt, to keep your photos secure. Photok is completely free, open source, and contains no ads.
 pass import is a password store extension allowing you to import your password database to a password store repository conveniently. It natively supports import from 20 different password managers. More manager support can easily be added.
pass import is a password store extension allowing you to import your password database to a password store repository conveniently. It natively supports import from 20 different password managers. More manager support can easily be added.
 Due to the structure of pass, file- and directory names are not encrypted in the password store. pass-tomb provides a convenient solution to put your password store in a tomb and then keep your password tree encrypted when you are not using it. It uses the same GPG key to encrypt passwords and tomb, therefore you don't need to manage more key or secret. Moreover, you can ask pass-tomb to automatically close your store after a given time.
Due to the structure of pass, file- and directory names are not encrypted in the password store. pass-tomb provides a convenient solution to put your password store in a tomb and then keep your password tree encrypted when you are not using it. It uses the same GPG key to encrypt passwords and tomb, therefore you don't need to manage more key or secret. Moreover, you can ask pass-tomb to automatically close your store after a given time.
 MikroLock reads and writes encrypted miniLock files. It is a fast native implementation of the open minilock file format. Despite its name (and in contrast to the original implementation), it can also handle big files. Information about the cryptographic details: https://minilock.io.
MikroLock reads and writes encrypted miniLock files. It is a fast native implementation of the open minilock file format. Despite its name (and in contrast to the original implementation), it can also handle big files. Information about the cryptographic details: https://minilock.io.
 sencrypt and sdecrypt are utilities for encrypting and decrypting data with the AES, DES, 3DES, and RC4 algorithms. It can read keys from files or ask for a passphrase and use that together with a salt to derive a key using the PBKDF2 key derivation function. sencrypt and sdecrypt are portable and compatible reimplementations of the encrypt and decrypt utilities in Solaris/Illumos-based operating systems.
sencrypt and sdecrypt are utilities for encrypting and decrypting data with the AES, DES, 3DES, and RC4 algorithms. It can read keys from files or ask for a passphrase and use that together with a salt to derive a key using the PBKDF2 key derivation function. sencrypt and sdecrypt are portable and compatible reimplementations of the encrypt and decrypt utilities in Solaris/Illumos-based operating systems.
 Zenroom is a brand new, small and portable virtual machine for cryptographic operations. The Zenroom VM has no external dependencies, is smaller than 2MB, runs in even less memory and is ready for experimental use on many target platforms: desktop, embedded, mobile, cloud and browsers (webassembly). The goal of this project is that of improving people's awareness of how their data is processed by algorithms, as well facilitate the work of developers to create along privacy by design principles
Zenroom is a brand new, small and portable virtual machine for cryptographic operations. The Zenroom VM has no external dependencies, is smaller than 2MB, runs in even less memory and is ready for experimental use on many target platforms: desktop, embedded, mobile, cloud and browsers (webassembly). The goal of this project is that of improving people's awareness of how their data is processed by algorithms, as well facilitate the work of developers to create along privacy by design principles
 This script makes it easy to create an initial environment setup for secure GitHub exchanges.
This script makes it easy to create an initial environment setup for secure GitHub exchanges.
 heads is a libre (free as in freedom) GNU/Linux distribution. It aims to be a distro that respects your privacy, freedom, and helps you to stay secure and anonymous. It runs on GNU/Linux with kernel patches -libre and -grsec, runs live with a persistence mode powered by Tomb and routes all its traffic through Tor.
heads is a libre (free as in freedom) GNU/Linux distribution. It aims to be a distro that respects your privacy, freedom, and helps you to stay secure and anonymous. It runs on GNU/Linux with kernel patches -libre and -grsec, runs live with a persistence mode powered by Tomb and routes all its traffic through Tor.
 Secrets can be used to split a secret text into shares to be distributed to friends. When all friends agree, the shares can be combined to retrieve the original secret text, for instance to give consensual access to a lost pin, a password, a list of passwords, a private document or a key to an encrypted volume. Secret sharing can be useful in many different situations and this tool is a simple and well documented free and open source implementation available for anyone to use from this website,
Secrets can be used to split a secret text into shares to be distributed to friends. When all friends agree, the shares can be combined to retrieve the original secret text, for instance to give consensual access to a lost pin, a password, a list of passwords, a private document or a key to an encrypted volume. Secret sharing can be useful in many different situations and this tool is a simple and well documented free and open source implementation available for anyone to use from this website,
 Naamari is AES&SHA-based crypto-synchronizer for cloud/remote file storage, with cryptographic and transport modules being separate applications. It works with 4 locations. 1st: local dir with original files. 2nd: dir containing folder structure and names of files placed into storage (but not content). 3rd & 4th - storages: local (another local dir) and remote (say, a cloud). In storages, there are no folders, files have pseudo-random names and encrypted content ("flattening"). The main module
Naamari is AES&SHA-based crypto-synchronizer for cloud/remote file storage, with cryptographic and transport modules being separate applications. It works with 4 locations. 1st: local dir with original files. 2nd: dir containing folder structure and names of files placed into storage (but not content). 3rd & 4th - storages: local (another local dir) and remote (say, a cloud). In storages, there are no folders, files have pseudo-random names and encrypted content ("flattening"). The main module
 gpgpwd is a terminal-based password manager. It stores a list of passwords and their associated usernames in a GnuPG-encrypted file, and allows you to easily retrieve, change, and add to that file as needed. It also generates random passwords which you can use, easily allowing you to have one "master password" (for your gpg key), with one unique and random password for each website or service you use, ensuring that your other accounts stay safe even if one password gets leaked. gpgpwd can als
gpgpwd is a terminal-based password manager. It stores a list of passwords and their associated usernames in a GnuPG-encrypted file, and allows you to easily retrieve, change, and add to that file as needed. It also generates random passwords which you can use, easily allowing you to have one "master password" (for your gpg key), with one unique and random password for each website or service you use, ensuring that your other accounts stay safe even if one password gets leaked. gpgpwd can als
 Briefly, t1ha is a 64-bit Hash Function: 1. Created for 64-bit little-endian platforms, in predominantly for x86_64, but without penalties could runs on any 64-bit CPU. 2. In most cases up to 15% faster than City64, xxHash, mum-hash, metro-hash and all others which are not use specific hardware tricks. 3. Not suitable for cryptography.
Briefly, t1ha is a 64-bit Hash Function: 1. Created for 64-bit little-endian platforms, in predominantly for x86_64, but without penalties could runs on any 64-bit CPU. 2. In most cases up to 15% faster than City64, xxHash, mum-hash, metro-hash and all others which are not use specific hardware tricks. 3. Not suitable for cryptography.
 C implementation of NTRUEncrypt An implementation of the public-key encryption scheme NTRUEncrypt in C. NTRUEncrypt's main strengths are high performance and resistance to quantum computer attacks. Its main drawback is that it is patent encumbered. The patents expire in 2020; when built with the NTRU_AVOID_HAMMING_WT_PATENT flag, libntru becomes patent-free in 2017. For more information on the NTRUEncrypt algorithm, see the NTRU introduction page at http://tbuktu.github.com/ntru/
C implementation of NTRUEncrypt An implementation of the public-key encryption scheme NTRUEncrypt in C. NTRUEncrypt's main strengths are high performance and resistance to quantum computer attacks. Its main drawback is that it is patent encumbered. The patents expire in 2020; when built with the NTRU_AVOID_HAMMING_WT_PATENT flag, libntru becomes patent-free in 2017. For more information on the NTRUEncrypt algorithm, see the NTRU introduction page at http://tbuktu.github.com/ntru/
 Dowse is a transparent proxy facilitating the awareness of ingoing and outgoing connections, from, to, and within a local area network. Dowse provides a central point of soft control for all local traffic: from ARP traffic (layer 2) to TCP/IP (layers 3 and 4) as well as application space, by chaining a firewall setup to a trasparent proxy setup. A core feature for Dowse is that of hiding all the complexity of such a setup.
Dowse is a transparent proxy facilitating the awareness of ingoing and outgoing connections, from, to, and within a local area network. Dowse provides a central point of soft control for all local traffic: from ARP traffic (layer 2) to TCP/IP (layers 3 and 4) as well as application space, by chaining a firewall setup to a trasparent proxy setup. A core feature for Dowse is that of hiding all the complexity of such a setup.
 Jaro Mail is an integrated suite of interoperable tools for GNU/Linux and Apple/OSX to manage e-mail communication in a private and efficient way, without relying too much on on-line services, in fact encouraging users to store e-mail locally. Rather than reinventing the wheel, Jaro Mail reuses some existing free and open source tools working since more than 10 years, generating their configurations and setting up integrations automatically.
Jaro Mail is an integrated suite of interoperable tools for GNU/Linux and Apple/OSX to manage e-mail communication in a private and efficient way, without relying too much on on-line services, in fact encouraging users to store e-mail locally. Rather than reinventing the wheel, Jaro Mail reuses some existing free and open source tools working since more than 10 years, generating their configurations and setting up integrations automatically.
 This is a scoring server built using Ruby on Rails by the Military Cyber Professionals Association (MCPA). It is free to use and extend under the MIT license. The goal of this project is to provide a standard generic scoring server that provides an easy way to add and modify problems and track statistics of a Cyber Capture the Flag event.
This is a scoring server built using Ruby on Rails by the Military Cyber Professionals Association (MCPA). It is free to use and extend under the MIT license. The goal of this project is to provide a standard generic scoring server that provides an easy way to add and modify problems and track statistics of a Cyber Capture the Flag event.
 CACKey provides a standard interface (PKCS#11) for smartcards connected to a PC/SC compliant reader. It performs a similar function to "CoolKey", but only supports Government Smartcards. It supports all Government Smartcards that implement the Government Smartcard Interoperability Specification (GSC-IS) v2.1 or newer.
CACKey provides a standard interface (PKCS#11) for smartcards connected to a PC/SC compliant reader. It performs a similar function to "CoolKey", but only supports Government Smartcards. It supports all Government Smartcards that implement the Government Smartcard Interoperability Specification (GSC-IS) v2.1 or newer.
 mlock reads and writes encrypted miniLock files. It is a fast native implementation of the minilock file format. Despite its name (and in contrast to the original implementation), it can also handle big files. Information about the cryptographic details: https://minilock.io.
mlock reads and writes encrypted miniLock files. It is a fast native implementation of the minilock file format. Despite its name (and in contrast to the original implementation), it can also handle big files. Information about the cryptographic details: https://minilock.io.
 JSch is a pure Java implementation of SSH2. It allows you to connect to an sshd server and use port forwarding, X11 forwarding, file transfer, etc. You can integrate its functionality into your own Java programs.
JSch is a pure Java implementation of SSH2. It allows you to connect to an sshd server and use port forwarding, X11 forwarding, file transfer, etc. You can integrate its functionality into your own Java programs.
 The OpenSSL Project is a collaborative effort to develop a robust, commercial-grade, fully featured, and Open Source toolkit implementing the Secure Sockets Layer (SSLv2/v3) and Transport Layer Security (TLSv1) as well as a full-strength general-purpose cryptography library.
The OpenSSL Project is a collaborative effort to develop a robust, commercial-grade, fully featured, and Open Source toolkit implementing the Secure Sockets Layer (SSLv2/v3) and Transport Layer Security (TLSv1) as well as a full-strength general-purpose cryptography library.
 gcaff is a graphical OpenPGP/GPG key signing tool. It simplifies signing multiple keys, as it was intended for keysigning parties. It displays photo IDs for easier identification, and allows multi-key signing in one go. Certification levels can be adapted on a per-key basis, and it includes automatic emailing the final signed keys.
gcaff is a graphical OpenPGP/GPG key signing tool. It simplifies signing multiple keys, as it was intended for keysigning parties. It displays photo IDs for easier identification, and allows multi-key signing in one go. Certification levels can be adapted on a per-key basis, and it includes automatic emailing the final signed keys.
 ZShaolin unleashes the power of GNU/Linux on your Android phone or tablet by installing a small and powerful shell environment. It comes with applications to edit images, audio and video using batch scripts one can write and upload. It does not require rooting, not even an Internet connection to work.
ZShaolin unleashes the power of GNU/Linux on your Android phone or tablet by installing a small and powerful shell environment. It comes with applications to edit images, audio and video using batch scripts one can write and upload. It does not require rooting, not even an Internet connection to work.
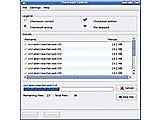 Checksum Control is a wizard to generate and verify checksum files. It supports SFV and MD5, even some exotic MD5 meta file types.
Checksum Control is a wizard to generate and verify checksum files. It supports SFV and MD5, even some exotic MD5 meta file types.
 A pure C library for asymmetric cryptography algorithm.Include Modified-Rabin signature scheme,Rabin encryption scheme,H. C. Williams encryption scheme.
A pure C library for asymmetric cryptography algorithm.Include Modified-Rabin signature scheme,Rabin encryption scheme,H. C. Williams encryption scheme.
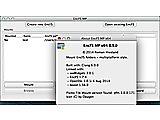 EncFSMP allows to mount and edit/create an EncFS (encrypted file system) on Windows or Max OS X systems. It's compatible to Linux encfs 1.7.4, but includes the proprietary Pismo File Mount kernel driver for Windows.
EncFSMP allows to mount and edit/create an EncFS (encrypted file system) on Windows or Max OS X systems. It's compatible to Linux encfs 1.7.4, but includes the proprietary Pismo File Mount kernel driver for Windows.
 Web-based password manager that does not store any passwords.
Web-based password manager that does not store any passwords.
 miniLock was subjected to a cryptographic code audit carried out by Cure53 and with the support of the Open Technology Fund.
miniLock was subjected to a cryptographic code audit carried out by Cure53 and with the support of the Open Technology Fund.
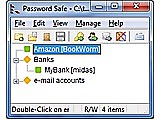 Password Safe is a password database utility. It stores multiple identities and accounts encrypted using Bruce Schneiers Twofish behind a master key. It provides an intuitive user interface, automatic backups, and is available on many plattforms.
Password Safe is a password database utility. It stores multiple identities and accounts encrypted using Bruce Schneiers Twofish behind a master key. It provides an intuitive user interface, automatic backups, and is available on many plattforms.
 PolarSSL is a light-weight cryptographic and SSL/TLS library written in C. PolarSSL makes it easy for developers to include cryptographic and SSL/TLS capabilities in their (embedded) applications with as little hassle as possible. Loose coupling of the components inside the library means that it is easy to separate the parts that are needed, without needing to include the total library. PolarSSL is written with embedded systems in mind and has been ported on a number of architectures, including
PolarSSL is a light-weight cryptographic and SSL/TLS library written in C. PolarSSL makes it easy for developers to include cryptographic and SSL/TLS capabilities in their (embedded) applications with as little hassle as possible. Loose coupling of the components inside the library means that it is easy to separate the parts that are needed, without needing to include the total library. PolarSSL is written with embedded systems in mind and has been ported on a number of architectures, including
|