 AdGuard Home is a network-wide software for blocking ads & tracking. After you set it up, it’ll cover ALL your home devices, and you don’t need any client-side software for that. With the rise of Internet-Of-Things and connected devices, it becomes more and more important to be able to control your whole network.
AdGuard Home is a network-wide software for blocking ads & tracking. After you set it up, it’ll cover ALL your home devices, and you don’t need any client-side software for that. With the rise of Internet-Of-Things and connected devices, it becomes more and more important to be able to control your whole network.
 pimhasher is a program inspired by VeraCrypt's PIM (Personal Iterations Multiplier) feature, designed to provide the same functionality for LUKS (Linux Unified Key Setup)
pimhasher is a program inspired by VeraCrypt's PIM (Personal Iterations Multiplier) feature, designed to provide the same functionality for LUKS (Linux Unified Key Setup)
 Snort is the foremost Open Source Intrusion Prevention System (IPS) in the world. Snort IPS uses a series of rules that help define malicious network activity and uses those rules to find packets that match against them and generates alerts for users. Snort can be deployed inline to stop these packets, as well. Snort has three primary uses: As a packet sniffer like tcpdump, as a packet logger — which is useful for network traffic debugging, or it can be used as a full-blown network intrusion pr
Snort is the foremost Open Source Intrusion Prevention System (IPS) in the world. Snort IPS uses a series of rules that help define malicious network activity and uses those rules to find packets that match against them and generates alerts for users. Snort can be deployed inline to stop these packets, as well. Snort has three primary uses: As a packet sniffer like tcpdump, as a packet logger — which is useful for network traffic debugging, or it can be used as a full-blown network intrusion pr
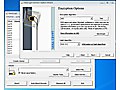 VeraCrypt is a full-disk encryption software derived from TrueCrypt. It revises some of the algorithm usage against brute-force attacks. For example system partitions use use larger rounds of PBKDF2 key stretching. The partition and container format is different to that of TrueCrypt however.
VeraCrypt is a full-disk encryption software derived from TrueCrypt. It revises some of the algorithm usage against brute-force attacks. For example system partitions use use larger rounds of PBKDF2 key stretching. The partition and container format is different to that of TrueCrypt however.
 ClamAV is an anti-virus engine, which is commonly used for email and web scanning, or gateway and fileserver securing. It provides a command-line scanner, a sendmail milter, automatic signature database updates, built-in support for many archiving and container or mail encoding formats, scanning standard ELF and compressed executables, as well as common office document formats.
ClamAV is an anti-virus engine, which is commonly used for email and web scanning, or gateway and fileserver securing. It provides a command-line scanner, a sendmail milter, automatic signature database updates, built-in support for many archiving and container or mail encoding formats, scanning standard ELF and compressed executables, as well as common office document formats.
 KeePassXC is a modern, secure, and open-source password manager that stores and manages your most sensitive information. You can run KeePassXC on Windows, macOS, and Linux systems. KeePassXC is for people with extremely high demands of secure personal data management. It saves many different types of information, such as usernames, passwords, URLs, attachments, and notes in an offline, encrypted file that can be stored in any location, including private and public cloud solutions. For easy ident
KeePassXC is a modern, secure, and open-source password manager that stores and manages your most sensitive information. You can run KeePassXC on Windows, macOS, and Linux systems. KeePassXC is for people with extremely high demands of secure personal data management. It saves many different types of information, such as usernames, passwords, URLs, attachments, and notes in an offline, encrypted file that can be stored in any location, including private and public cloud solutions. For easy ident
 The OpenBSD rpki-client is a free, easy-to-use implementation of the Resource Public Key Infrastructure (RPKI) for Relying Parties (RP) to facilitate validation of the Route Origin of a BGP announcement. The program queries the RPKI repository system, downloads and validates Route Origin Authorisations (ROAs) and finally outputs Validated ROA Payloads (VRPs) in the configuration format of OpenBGPD, BIRD, and also as CSV or JSON objects for consumption by other routing stacks.
The OpenBSD rpki-client is a free, easy-to-use implementation of the Resource Public Key Infrastructure (RPKI) for Relying Parties (RP) to facilitate validation of the Route Origin of a BGP announcement. The program queries the RPKI repository system, downloads and validates Route Origin Authorisations (ROAs) and finally outputs Validated ROA Payloads (VRPs) in the configuration format of OpenBGPD, BIRD, and also as CSV or JSON objects for consumption by other routing stacks.
 The stunnel program works as SSL encryption wrapper between remote and local network sockets or inetd-started daemons. It adds SSL or TLS functionality to any network service, commonly POP3, IMAP or HTTP servers. Stunnel uses OpenSSL for cryptography. It can itself function as port redirection deamon, or as temporary traffic interceptor, and requires no adaption of the shadowed programs.
The stunnel program works as SSL encryption wrapper between remote and local network sockets or inetd-started daemons. It adds SSL or TLS functionality to any network service, commonly POP3, IMAP or HTTP servers. Stunnel uses OpenSSL for cryptography. It can itself function as port redirection deamon, or as temporary traffic interceptor, and requires no adaption of the shadowed programs.
 Samhain is a file integrity / intrusion detection system that can be used on single hosts as well as on networks. It been designed to monitor multiple hosts with potentially different operating systems, providing centralized logging and baseline database storage, although it can also be used as standalone application on a single host.
Samhain is a file integrity / intrusion detection system that can be used on single hosts as well as on networks. It been designed to monitor multiple hosts with potentially different operating systems, providing centralized logging and baseline database storage, although it can also be used as standalone application on a single host.
 ALT is a set of Linux distributions based on Sisyphus, an APT-enabled RPM package repository that aims to achieve feature completeness, usability, and security in a sensible and manageable mixture.
ALT is a set of Linux distributions based on Sisyphus, an APT-enabled RPM package repository that aims to achieve feature completeness, usability, and security in a sensible and manageable mixture.
 Hashrat is a command-line utility that hashes things using md5, sha1/256/512, whirlpool and jh hash algorithms. It's written in C with few dependancies (basically just the standard C library). It can read input from standard in and hash it, either as a complete file, or line-by-line. It can recursively hash files on disk, either outputing hashes to stdout, or storing them in filesystem attributes, or in a memcached server. It can check files against a list of hashes supplied on stdin, or in t
Hashrat is a command-line utility that hashes things using md5, sha1/256/512, whirlpool and jh hash algorithms. It's written in C with few dependancies (basically just the standard C library). It can read input from standard in and hash it, either as a complete file, or line-by-line. It can recursively hash files on disk, either outputing hashes to stdout, or storing them in filesystem attributes, or in a memcached server. It can check files against a list of hashes supplied on stdin, or in t
 Contextal Platform is a powerful open-source technology designed for advanced threat detection and intelligence. The platform’s contextual threat detection capabilities enable users to develop situational scenarios using ContexQL, a dedicated language designed with flexibility and performance in mind. These scenarios draw on global context, metadata, relationships, time, anomalies, content, and other factors to trigger specific actions. This layered, contextual approach allows for more adaptive
Contextal Platform is a powerful open-source technology designed for advanced threat detection and intelligence. The platform’s contextual threat detection capabilities enable users to develop situational scenarios using ContexQL, a dedicated language designed with flexibility and performance in mind. These scenarios draw on global context, metadata, relationships, time, anomalies, content, and other factors to trigger specific actions. This layered, contextual approach allows for more adaptive
 LibreSSL Portable is a free version of the SSL/TLS protocol forked from OpenSSL, and developed by the OpenBSD project. LibreSSL is developed as part of the OpenBSD system, with lots of ancient cruft and security woes already fixed. The portable version for other Unices is developed alongside.
LibreSSL Portable is a free version of the SSL/TLS protocol forked from OpenSSL, and developed by the OpenBSD project. LibreSSL is developed as part of the OpenBSD system, with lots of ancient cruft and security woes already fixed. The portable version for other Unices is developed alongside.
 The Mandos system allows computers to have encrypted root file systems and at the same time be capable of remote or unattended reboots. The computers run a small client program in the initial RAM disk environment which will communicate with a server over a network. All network communication is encrypted using TLS. The clients are identified by the server using a TLS key that is unique to each client. The server sends the clients an encrypted password. The encrypted password is decrypted by the c
The Mandos system allows computers to have encrypted root file systems and at the same time be capable of remote or unattended reboots. The computers run a small client program in the initial RAM disk environment which will communicate with a server over a network. All network communication is encrypted using TLS. The clients are identified by the server using a TLS key that is unique to each client. The server sends the clients an encrypted password. The encrypted password is decrypted by the c
 OpenSSH is a BSD/Linux implementation of SSH1 and SSH2 for encrypted terminal connections, tunneling and file transfers. It includes the sshd server, scp and sftp, and various utility tools such as ssh-add, ssh-agent, ssh-keysign, ssh-keyscan, ssh-keygen, and the sftp-server.
OpenSSH is a BSD/Linux implementation of SSH1 and SSH2 for encrypted terminal connections, tunneling and file transfers. It includes the sshd server, scp and sftp, and various utility tools such as ssh-add, ssh-agent, ssh-keysign, ssh-keyscan, ssh-keygen, and the sftp-server.
 PacketFence is a network access control (NAC) manager. It includes numerous features, including user registration and sanitation, central wireless and cable-network control, BYOD (bring-your-own-device) configuration, 802.1X support, and layer-2 device isolation. PacketFence is useful for managing small to large networks and intranet-access points.
PacketFence is a network access control (NAC) manager. It includes numerous features, including user registration and sanitation, central wireless and cable-network control, BYOD (bring-your-own-device) configuration, 802.1X support, and layer-2 device isolation. PacketFence is useful for managing small to large networks and intranet-access points.
 The Universal Radio Hacker (URH) is a complete suite for wireless protocol investigation with native support for many common Software Defined Radios. URH allows easy demodulation of signals combined with an automatic detection of modulation parameters making it a breeze to identify the bits and bytes that fly over the air. As data often gets encoded before transmission, URH offers customizable decodings to crack even sophisticated encodings like CC1101 data whitening. When it comes to protocol r
The Universal Radio Hacker (URH) is a complete suite for wireless protocol investigation with native support for many common Software Defined Radios. URH allows easy demodulation of signals combined with an automatic detection of modulation parameters making it a breeze to identify the bits and bytes that fly over the air. As data often gets encoded before transmission, URH offers customizable decodings to crack even sophisticated encodings like CC1101 data whitening. When it comes to protocol r
 Afick is a fast and portable intrusion detection and integrity monitoring system, designed to work on all platforms (it only needs Perl and a few standard modules), including Windows, Linux, Unix. The configuration syntax is very close from tripwire/aide.
Afick is a fast and portable intrusion detection and integrity monitoring system, designed to work on all platforms (it only needs Perl and a few standard modules), including Windows, Linux, Unix. The configuration syntax is very close from tripwire/aide.
 Tomb is a system to make strong encryption easy for everyday use. A tomb is like a locked folder that can be safely transported and hidden in a filesystem. Its keys can be kept separate; for example, you can keep the tomb on your computer and its key on a USB stick. Tomb is written in code that is easy to review and links shared components: it consists of a ZShell script and desktop integration apps; it uses standard GNU tools and the crypto API of the Linux kernel (dm-crypt) via cryptsetup.
Tomb is a system to make strong encryption easy for everyday use. A tomb is like a locked folder that can be safely transported and hidden in a filesystem. Its keys can be kept separate; for example, you can keep the tomb on your computer and its key on a USB stick. Tomb is written in code that is easy to review and links shared components: it consists of a ZShell script and desktop integration apps; it uses standard GNU tools and the crypto API of the Linux kernel (dm-crypt) via cryptsetup.
 Calendar Lock PEA displays password encrypted iCalendar compatible calendars in monthly, weekly and daily view with optional cloud connection. The calendars are always encrypted on the device or in the cloud. iCalendars from other applications can be imported.
Calendar Lock PEA displays password encrypted iCalendar compatible calendars in monthly, weekly and daily view with optional cloud connection. The calendars are always encrypted on the device or in the cloud. iCalendars from other applications can be imported.
 Delegate accurate least privilege access with ease. Express easily with a regex and expose only what is needed and nothing more. Or validate file edits with pleaseedit. Admin your box without giving users full root shells, most admins have experience of regex in one form or another, so lets configure access that way.
Delegate accurate least privilege access with ease. Express easily with a regex and expose only what is needed and nothing more. Or validate file edits with pleaseedit. Admin your box without giving users full root shells, most admins have experience of regex in one form or another, so lets configure access that way.
 OnionShare is an open source tool that lets you securely and anonymously share files, host websites, and chat with friends using the Tor network.
OnionShare is an open source tool that lets you securely and anonymously share files, host websites, and chat with friends using the Tor network.
 Shorewall is a flexible firewall configuration system for Linux 2.4/3.x iptables. It's suitable for routers, gateways, servers, VPN environments and just desktop systems. It provides a higher level rule-based configuration scheme to configure the Netfilter kernel module, routes, interfaces and traffic shaping. It supports both IPv4 and IPv6.
Shorewall is a flexible firewall configuration system for Linux 2.4/3.x iptables. It's suitable for routers, gateways, servers, VPN environments and just desktop systems. It provides a higher level rule-based configuration scheme to configure the Netfilter kernel module, routes, interfaces and traffic shaping. It supports both IPv4 and IPv6.
 Cyberprobe is a network attack monitoring software stack. It collects data packets for inspection, logging and analysis. It can be integrated with snort to record the actual intrusion source. While Cybermon is highly configurable protocol decoder and analysis tool, which can also automate responses such as dynamic connection resets, firewalling or forged DNS replies.
Cyberprobe is a network attack monitoring software stack. It collects data packets for inspection, logging and analysis. It can be integrated with snort to record the actual intrusion source. While Cybermon is highly configurable protocol decoder and analysis tool, which can also automate responses such as dynamic connection resets, firewalling or forged DNS replies.
 The Enrollment over Secure Transport (EST) protocol describes a simple, yet functional, certificate management protocol targeting Public Key Infrastructure (PKI) clients that need to acquire client certificates and associated Certification Authority (CA) certificates. This protocol supports both client-generated public/private key pairs and those generated by the CA. The nginx-http-est module provides EST functionality for a Nginx server.
The Enrollment over Secure Transport (EST) protocol describes a simple, yet functional, certificate management protocol targeting Public Key Infrastructure (PKI) clients that need to acquire client certificates and associated Certification Authority (CA) certificates. This protocol supports both client-generated public/private key pairs and those generated by the CA. The nginx-http-est module provides EST functionality for a Nginx server.
 GnuPG (the GNU Privacy Guard or GPG) is GNU's tool for secure communication and data storage. It can be used to encrypt data and to create digital signatures. It includes an advanced key management facility and is compliant with the proposed OpenPGP Internet standard as described in RFC2440. As such, it is meant to be compatible with PGP from NAI, Inc. Because it does not use any patented algorithms, it can be used without any restrictions.
GnuPG (the GNU Privacy Guard or GPG) is GNU's tool for secure communication and data storage. It can be used to encrypt data and to create digital signatures. It includes an advanced key management facility and is compliant with the proposed OpenPGP Internet standard as described in RFC2440. As such, it is meant to be compatible with PGP from NAI, Inc. Because it does not use any patented algorithms, it can be used without any restrictions.
 sshdo - controls which commands may be executed via incoming ssh. sshdo provides an easily configurable way of controlling which commands may be executed via incoming ssh connections by specific users and specific keys. Training mode allows a key to be used for any command, while logging them. Then sshdo can learn from the logs to know what commands to allow. It can also unlearn commands that are no longer in use. This mitigates against private ssh key compromise with very little effort.
sshdo - controls which commands may be executed via incoming ssh. sshdo provides an easily configurable way of controlling which commands may be executed via incoming ssh connections by specific users and specific keys. Training mode allows a key to be used for any command, while logging them. Then sshdo can learn from the logs to know what commands to allow. It can also unlearn commands that are no longer in use. This mitigates against private ssh key compromise with very little effort.
 PyMOSP is a Python library to access MOSP (MONARC Objects Sharing Platform). It also works as a command line tool (using environment vars for application url and access token.)
PyMOSP is a Python library to access MOSP (MONARC Objects Sharing Platform). It also works as a command line tool (using environment vars for application url and access token.)
 GPOA (GPO Applier) is a utility to fetch, reinterpret and apply GPOs from Windows Active Directory domains in UNIX environments.
GPOA (GPO Applier) is a utility to fetch, reinterpret and apply GPOs from Windows Active Directory domains in UNIX environments.
 Firejail is a security sandbox tool, which utilizes Linux 3.x namespaces to setup restricted environments for untrusted applications. It works for console and graphical applications, servers, or even login sessions; by assigning them and their subprocesses a private view of globally shared kernel resources. Firejail isolates mount points, adds chrooting, filesystem writability or overlays, sandbox filesystem sharing, networking stack and firewall isolation, constrains interprocess communication,
Firejail is a security sandbox tool, which utilizes Linux 3.x namespaces to setup restricted environments for untrusted applications. It works for console and graphical applications, servers, or even login sessions; by assigning them and their subprocesses a private view of globally shared kernel resources. Firejail isolates mount points, adds chrooting, filesystem writability or overlays, sandbox filesystem sharing, networking stack and firewall isolation, constrains interprocess communication,
 Browser Notebook displays, encrypts and stores notes locally in the Web browser. Unlike similar programs, the texts are stored nowhere else than in your browser and always in encrypted form. The plaintext is kept in memory only. You can either use the online version without any registration or installation, or you can download the offline version and use it without Internet access.
Browser Notebook displays, encrypts and stores notes locally in the Web browser. Unlike similar programs, the texts are stored nowhere else than in your browser and always in encrypted form. The plaintext is kept in memory only. You can either use the online version without any registration or installation, or you can download the offline version and use it without Internet access.
 PAM autologin module
PAM autologin module
 MONARC - Method for an optimised analysis of risks
MONARC - Method for an optimised analysis of risks
 Notebook PEA protects texts using authenticated encryption (EAX mode) for confidentiality, integrity, and authenticity of the text. Notebook PEA works like a self-decrypting archive (SDA): the plaintext is never stored on disk, instead it is displayed in a simple text editor with some styling functionality, redo/undo and copy, cut, paste commands. Supports access to Nextcloud, Owncloud and other cloud providers that support the WebDAV protocol.
Notebook PEA protects texts using authenticated encryption (EAX mode) for confidentiality, integrity, and authenticity of the text. Notebook PEA works like a self-decrypting archive (SDA): the plaintext is never stored on disk, instead it is displayed in a simple text editor with some styling functionality, redo/undo and copy, cut, paste commands. Supports access to Nextcloud, Owncloud and other cloud providers that support the WebDAV protocol.
 File Lock PEA encrypt files or folders, using authenticated encryption (EAX mode) to provide both confidentiality and the integrity and memory-hard key derivation functions to protect custom hardware attacks. Nextcloud, Owncloud and some cloud providers are supported. File Lock PEA is platform-independent, needs no installation but requires the Java Runtime Environment.
File Lock PEA encrypt files or folders, using authenticated encryption (EAX mode) to provide both confidentiality and the integrity and memory-hard key derivation functions to protect custom hardware attacks. Nextcloud, Owncloud and some cloud providers are supported. File Lock PEA is platform-independent, needs no installation but requires the Java Runtime Environment.
 Freshermeat is an open source software directory and release tracker. Main functionalities are the following: - tracking of software releases, vulnerabilities (CVE) and news; - subscribe to releases of a project or an organization via an ATOM feed; - JSON-based API in order to manages projects, releases, CVEs, etc.; - management of organizations.
Freshermeat is an open source software directory and release tracker. Main functionalities are the following: - tracking of software releases, vulnerabilities (CVE) and news; - subscribe to releases of a project or an organization via an ATOM feed; - JSON-based API in order to manages projects, releases, CVEs, etc.; - management of organizations.
 hdparm - get/set ATA/SATA drive parameters under Linux
hdparm - get/set ATA/SATA drive parameters under Linux
 MOSP is a platform to create, edit and share JSON objects. The goal is to gather security related JSON objects, in the first place aimed to be used with MONARC. You can use any available schemas in order to create new JSON objects.
MOSP is a platform to create, edit and share JSON objects. The goal is to gather security related JSON objects, in the first place aimed to be used with MONARC. You can use any available schemas in order to create new JSON objects.
 pass import is a password store extension allowing you to import your password database to a password store repository conveniently. It natively supports import from 20 different password managers. More manager support can easily be added.
pass import is a password store extension allowing you to import your password database to a password store repository conveniently. It natively supports import from 20 different password managers. More manager support can easily be added.
 Due to the structure of pass, file- and directory names are not encrypted in the password store. pass-tomb provides a convenient solution to put your password store in a tomb and then keep your password tree encrypted when you are not using it. It uses the same GPG key to encrypt passwords and tomb, therefore you don't need to manage more key or secret. Moreover, you can ask pass-tomb to automatically close your store after a given time.
Due to the structure of pass, file- and directory names are not encrypted in the password store. pass-tomb provides a convenient solution to put your password store in a tomb and then keep your password tree encrypted when you are not using it. It uses the same GPG key to encrypt passwords and tomb, therefore you don't need to manage more key or secret. Moreover, you can ask pass-tomb to automatically close your store after a given time.
 This software aims to be a UNIX tool for generic secure usage when in need of privilege escalation. It is designed to run SUID, with "super-user powers" to execute things as root on the system it is installed. Main differences compared to sudo: - Easier audit thanks to literate development methodology - Fewer lines of code, fewer features, fewer dependencies - No configuration file, no parsers - Public domain licensing SUD is designed for security: it leverages all possible measures to avoid
This software aims to be a UNIX tool for generic secure usage when in need of privilege escalation. It is designed to run SUID, with "super-user powers" to execute things as root on the system it is installed. Main differences compared to sudo: - Easier audit thanks to literate development methodology - Fewer lines of code, fewer features, fewer dependencies - No configuration file, no parsers - Public domain licensing SUD is designed for security: it leverages all possible measures to avoid
 OPNsense is an open source, easy-to-use and easy-to-build FreeBSD based firewall and routing platform. OPNsense includes most of the features available in expensive commercial firewalls, and more in many cases. It brings the rich feature set of commercial offerings with the benefits of open and verifiable sources. OPNsense started as a fork of pfSense® and m0n0wall in 2014, with its first official release in January 2015. The project has evolved very quickly while still retaining familiar aspe
OPNsense is an open source, easy-to-use and easy-to-build FreeBSD based firewall and routing platform. OPNsense includes most of the features available in expensive commercial firewalls, and more in many cases. It brings the rich feature set of commercial offerings with the benefits of open and verifiable sources. OPNsense started as a fork of pfSense® and m0n0wall in 2014, with its first official release in January 2015. The project has evolved very quickly while still retaining familiar aspe
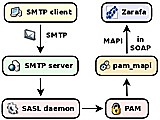 pam_mapi is a PAM module for authenticating against a Kopano or Zarafa server. It is intended to be used as a bridge between SASL daemons providing SMTP authentication and a Kopano/Zafara user information database.
pam_mapi is a PAM module for authenticating against a Kopano or Zarafa server. It is intended to be used as a bridge between SASL daemons providing SMTP authentication and a Kopano/Zafara user information database.
 Mimeguard allows the configuration of policy regarding filetypes allowed in email. It can unpack multipart emails and examine MS Office files for macros, HTML, PDF and RTF files for illegal strings and 'look into' .zip files to see what filetypes are within them. It uses a system of allowed/not allowed filetypes that are defined in a config file. It's intended to be used within a script or system-ed from a parent process and returns and exit code that indicates if a file/mail is considered safe
Mimeguard allows the configuration of policy regarding filetypes allowed in email. It can unpack multipart emails and examine MS Office files for macros, HTML, PDF and RTF files for illegal strings and 'look into' .zip files to see what filetypes are within them. It uses a system of allowed/not allowed filetypes that are defined in a config file. It's intended to be used within a script or system-ed from a parent process and returns and exit code that indicates if a file/mail is considered safe
 KeyBox is a web-based SSH console that centrally manages administrative access to systems. KeyBox combines key management and administration through profiles assigned to defined users.
KeyBox is a web-based SSH console that centrally manages administrative access to systems. KeyBox combines key management and administration through profiles assigned to defined users.
 Webfwlog is a Web-based firewall log reporting and analysis tool. It supports IPv6, as well as geoip data for ips using maxmind's geoip databases. It allows users to design reports to use on logged firewall data in whatever configuration they desire. Included are sample reports as a starting point. Reports can be sorted with a single click, or "drilled-down" all the way to the packet level, and report definitions saved for later use. Supported log formats are netfilter, ipfilter, ipfw, ipchains,
Webfwlog is a Web-based firewall log reporting and analysis tool. It supports IPv6, as well as geoip data for ips using maxmind's geoip databases. It allows users to design reports to use on logged firewall data in whatever configuration they desire. Included are sample reports as a starting point. Reports can be sorted with a single click, or "drilled-down" all the way to the packet level, and report definitions saved for later use. Supported log formats are netfilter, ipfilter, ipfw, ipchains,
 sencrypt and sdecrypt are utilities for encrypting and decrypting data with the AES, DES, 3DES, and RC4 algorithms. It can read keys from files or ask for a passphrase and use that together with a salt to derive a key using the PBKDF2 key derivation function. sencrypt and sdecrypt are portable and compatible reimplementations of the encrypt and decrypt utilities in Solaris/Illumos-based operating systems.
sencrypt and sdecrypt are utilities for encrypting and decrypting data with the AES, DES, 3DES, and RC4 algorithms. It can read keys from files or ask for a passphrase and use that together with a salt to derive a key using the PBKDF2 key derivation function. sencrypt and sdecrypt are portable and compatible reimplementations of the encrypt and decrypt utilities in Solaris/Illumos-based operating systems.
 Zenroom is a brand new, small and portable virtual machine for cryptographic operations. The Zenroom VM has no external dependencies, is smaller than 2MB, runs in even less memory and is ready for experimental use on many target platforms: desktop, embedded, mobile, cloud and browsers (webassembly). The goal of this project is that of improving people's awareness of how their data is processed by algorithms, as well facilitate the work of developers to create along privacy by design principles
Zenroom is a brand new, small and portable virtual machine for cryptographic operations. The Zenroom VM has no external dependencies, is smaller than 2MB, runs in even less memory and is ready for experimental use on many target platforms: desktop, embedded, mobile, cloud and browsers (webassembly). The goal of this project is that of improving people's awareness of how their data is processed by algorithms, as well facilitate the work of developers to create along privacy by design principles
 Python based milter for Sendmail and Postfix MTA servers to check incoming e-mails for Microsoft Office attachments. If a Microsoft Office document is attached to the e-mail, it will be scanned for suspicious VBA macro code. Files with malicious macros are, depending on configuration, either removed and replaced by harmless text files or alternatively the whole e-mail will be rejected.
Python based milter for Sendmail and Postfix MTA servers to check incoming e-mails for Microsoft Office attachments. If a Microsoft Office document is attached to the e-mail, it will be scanned for suspicious VBA macro code. Files with malicious macros are, depending on configuration, either removed and replaced by harmless text files or alternatively the whole e-mail will be rejected.
 pass update extends the pass utility with an update command providing an easy flow for updating passwords. It supports path, directory and wildcard update. Moreover, you can select how to update your passwords by automatically generating new passwords or manually setting your own.
pass update extends the pass utility with an update command providing an easy flow for updating passwords. It supports path, directory and wildcard update. Moreover, you can select how to update your passwords by automatically generating new passwords or manually setting your own.
 psad is an intrusion detection system built around iptables log messages to detect, alert, and (optionally) block port scans and other suspect traffic. For TCP scans psad analyzes TCP flags to determine the scan type (syn, fin, xmas, etc.) and corresponding command line options that could be supplied to nmap to generate such a scan. In addition, psad makes use of many TCP, UDP, and ICMP signatures contained within the Snort intrusion detection system (see http://www.snort.org/) to detect suspi
psad is an intrusion detection system built around iptables log messages to detect, alert, and (optionally) block port scans and other suspect traffic. For TCP scans psad analyzes TCP flags to determine the scan type (syn, fin, xmas, etc.) and corresponding command line options that could be supplied to nmap to generate such a scan. In addition, psad makes use of many TCP, UDP, and ICMP signatures contained within the Snort intrusion detection system (see http://www.snort.org/) to detect suspi
 A Phishing WIFI Rogue Captive Portal!
A Phishing WIFI Rogue Captive Portal!
 A command-line client for the haveibeenpwned.com API. Requires libUseful and libUseful-lua. Can list breaches, breaches for a specific account, and number of time a password has occured in breached data.
A command-line client for the haveibeenpwned.com API. Requires libUseful and libUseful-lua. Can list breaches, breaches for a specific account, and number of time a password has occured in breached data.
 MISP, Malware Information Sharing Platform and Threat Sharing, is an open source software solution for collecting, storing, distributing and sharing cyber security indicators and threat about cyber security incidents analysis and malware analysis. MISP is designed by and for incident analysts, security and ICT professionals or malware reverser to support their day-to-day operations to share structured informations efficiently.
MISP, Malware Information Sharing Platform and Threat Sharing, is an open source software solution for collecting, storing, distributing and sharing cyber security indicators and threat about cyber security incidents analysis and malware analysis. MISP is designed by and for incident analysts, security and ICT professionals or malware reverser to support their day-to-day operations to share structured informations efficiently.
 I2Pd is a lightweight C++ implementation of a I2P privacy network layer router. It provides pseudonymity for all routed application protocols, can be used for web browsing, IRC connections, and file transfers.
I2Pd is a lightweight C++ implementation of a I2P privacy network layer router. It provides pseudonymity for all routed application protocols, can be used for web browsing, IRC connections, and file transfers.
 Docker is an open platform for distributing software application in containers. It utilizes operating system-level virtualization for process and full resource isolation through cgroups, capabilities, SELinux, AppArmor, netfilter, and Linux kernel namespaces. Its libcontainer is based on libvirt and lxc. Docker Engine is the application and environment packaging tool. And Docker Hub is a cloud service for sharing prepackaged containers.
Docker is an open platform for distributing software application in containers. It utilizes operating system-level virtualization for process and full resource isolation through cgroups, capabilities, SELinux, AppArmor, netfilter, and Linux kernel namespaces. Its libcontainer is based on libvirt and lxc. Docker Engine is the application and environment packaging tool. And Docker Hub is a cloud service for sharing prepackaged containers.
 A lightweight implementation of the pinentry program used by gpg to ask for passwords. Can also replace ssh-askpass.
A lightweight implementation of the pinentry program used by gpg to ask for passwords. Can also replace ssh-askpass.
 Secrets can be used to split a secret text into shares to be distributed to friends. When all friends agree, the shares can be combined to retrieve the original secret text, for instance to give consensual access to a lost pin, a password, a list of passwords, a private document or a key to an encrypted volume. Secret sharing can be useful in many different situations and this tool is a simple and well documented free and open source implementation available for anyone to use from this website,
Secrets can be used to split a secret text into shares to be distributed to friends. When all friends agree, the shares can be combined to retrieve the original secret text, for instance to give consensual access to a lost pin, a password, a list of passwords, a private document or a key to an encrypted volume. Secret sharing can be useful in many different situations and this tool is a simple and well documented free and open source implementation available for anyone to use from this website,
 x509viewer is a simple command line application, written in Perl, that can be used to decode one or multiple X.509 certificates per given file, such as e.g. SSL certificates, CSRs (certificate signing requests), but also private keys.
x509viewer is a simple command line application, written in Perl, that can be used to decode one or multiple X.509 certificates per given file, such as e.g. SSL certificates, CSRs (certificate signing requests), but also private keys.
 x509watch is a simple command line application that can be used to list soon expiring or already expired X.509 certificates, such as SSL certificates. All certificates are searched by default in the standard PKI directory, but any other directory can be specified as a parameter. Only Base64 encoded DER and PEM X.509 certificates are supported.
x509watch is a simple command line application that can be used to list soon expiring or already expired X.509 certificates, such as SSL certificates. All certificates are searched by default in the standard PKI directory, but any other directory can be specified as a parameter. Only Base64 encoded DER and PEM X.509 certificates are supported.
 This software provides both a GO library implementing a Secret Sharing scheme and a command line tool which distributes and reconstructs your secret files.
This software provides both a GO library implementing a Secret Sharing scheme and a command line tool which distributes and reconstructs your secret files.
 WASP Seraphimdroid is a privacy and security protection app for Android devices. It enables users to protect their devices against malicious software (viruses, trojans, worms, etc.), phishing SMS, MMS messages, execution of dangerous USSD codes, theft and loosing. Also, it enables user to protect their privacy and to control the usage of applications and services via various kinds of locks. OWASP Seraphimdroid has two aims: To protect user's privacy and secure the device against malicious feat
WASP Seraphimdroid is a privacy and security protection app for Android devices. It enables users to protect their devices against malicious software (viruses, trojans, worms, etc.), phishing SMS, MMS messages, execution of dangerous USSD codes, theft and loosing. Also, it enables user to protect their privacy and to control the usage of applications and services via various kinds of locks. OWASP Seraphimdroid has two aims: To protect user's privacy and secure the device against malicious feat
 pam_honeycreds.so is a pam module that watches for particular passwords being used in login attempts. Simply watching for 'wrong' passwords can generate a lot of noise, due to people mistyping their passwords. With pam_honeycreds an admin can leave fake password lists around on their network, and then get an alert if any of those passwords are ever used. It can also be used to monitor for bruteforcers using the top passwords, or for internal passwords being used by bruteforcers against internet-
pam_honeycreds.so is a pam module that watches for particular passwords being used in login attempts. Simply watching for 'wrong' passwords can generate a lot of noise, due to people mistyping their passwords. With pam_honeycreds an admin can leave fake password lists around on their network, and then get an alert if any of those passwords are ever used. It can also be used to monitor for bruteforcers using the top passwords, or for internal passwords being used by bruteforcers against internet-
 SSHGuard is an automated log watcher which quickly sets up firewall blocks for detected brute-force attacks. It supports not just SSH, but also sendmail, exim, dovecot, Cucipop, UWimap, vsftpd, proftpd, pure-ftpd and FreeBSD ftpd. It understands syslog/-ng, metalog, multilog and raw log formats. And works with netfilter/iptables, PF, ipfw, or just hosts.allow to set up firewalling rules.
SSHGuard is an automated log watcher which quickly sets up firewall blocks for detected brute-force attacks. It supports not just SSH, but also sendmail, exim, dovecot, Cucipop, UWimap, vsftpd, proftpd, pure-ftpd and FreeBSD ftpd. It understands syslog/-ng, metalog, multilog and raw log formats. And works with netfilter/iptables, PF, ipfw, or just hosts.allow to set up firewalling rules.
 Fort integrates itself into the Windows file explorer. This allows you to easily encrypt (and decrypt) files via the Explorer context menu and to protect them with a password. All file types are supported. Fort can be also used to encrypt files in Onedrive, Dropbox and other similar services. Fort takes security seriously and uses AES with 256bit keys. On decryption Fort checks that the data is not tampered in any way and informs if data tampering is detected. For each file, Fort generates a ra
Fort integrates itself into the Windows file explorer. This allows you to easily encrypt (and decrypt) files via the Explorer context menu and to protect them with a password. All file types are supported. Fort can be also used to encrypt files in Onedrive, Dropbox and other similar services. Fort takes security seriously and uses AES with 256bit keys. On decryption Fort checks that the data is not tampered in any way and informs if data tampering is detected. For each file, Fort generates a ra
 DenyHost works to automatically block brute-force attacks against the secure shell service. It does this by scanning log files for failed login attempts and blocking remote hosts which have made too many failed connections.
DenyHost works to automatically block brute-force attacks against the secure shell service. It does this by scanning log files for failed login attempts and blocking remote hosts which have made too many failed connections.
 sup is a very small and secure C application. it is designed to run as root (with suid bit on) to facilitate the privilege escalation of users to execute certain programs as superuser. all settings in sup are hard-coded at compile time. sup is very portable and self-contained, designed for production use as a static binary. sup is a sort of hard-coded sudo: it is an ideal companion for artisans building small containers and embedded systems.
sup is a very small and secure C application. it is designed to run as root (with suid bit on) to facilitate the privilege escalation of users to execute certain programs as superuser. all settings in sup are hard-coded at compile time. sup is very portable and self-contained, designed for production use as a static binary. sup is a sort of hard-coded sudo: it is an ideal companion for artisans building small containers and embedded systems.
 etherpoke is a scriptable network session monitor. etherpoke defines three events: SESSION_BEGIN, SESSION_END, SESSION_ERROR to which a hook (system command) can be assigned. The event hook can be any program installed in the system. SESSION_BEGIN is triggered when the first packet matching the filter rule is captured. SESSION_END is triggered when the time since the last matching packet was captured exceeds the session timeout. SESSION_ERROR is triggered when it is no longer possible to pro
etherpoke is a scriptable network session monitor. etherpoke defines three events: SESSION_BEGIN, SESSION_END, SESSION_ERROR to which a hook (system command) can be assigned. The event hook can be any program installed in the system. SESSION_BEGIN is triggered when the first packet matching the filter rule is captured. SESSION_END is triggered when the time since the last matching packet was captured exceeds the session timeout. SESSION_ERROR is triggered when it is no longer possible to pro
 A linux PAM module that allows using USB flashdrives as authentcation tokens. Written mostly as a learning exercise, the code has been commented in the hope of providing a template to others interested in creating PAM modules. It can be used in combination with password authentication to prevent login or 'su' unless a particular usb-key is plugged into the system.
A linux PAM module that allows using USB flashdrives as authentcation tokens. Written mostly as a learning exercise, the code has been commented in the hope of providing a template to others interested in creating PAM modules. It can be used in combination with password authentication to prevent login or 'su' unless a particular usb-key is plugged into the system.
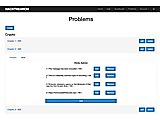 This is a scoring server built using Ruby on Rails by the Military Cyber Professionals Association (MCPA). It is free to use and extend under the MIT license. The goal of this project is to provide a standard generic scoring server that provides an easy way to add and modify problems and track statistics of a Cyber Capture the Flag event.
This is a scoring server built using Ruby on Rails by the Military Cyber Professionals Association (MCPA). It is free to use and extend under the MIT license. The goal of this project is to provide a standard generic scoring server that provides an easy way to add and modify problems and track statistics of a Cyber Capture the Flag event.
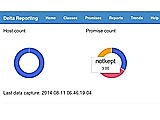 Delta Reporting is a central logging service for CFEngine. CFEngine promises and classes are stored in a central database and made available for advanced searches and reports via a modern Web interface and the command line.
Delta Reporting is a central logging service for CFEngine. CFEngine promises and classes are stored in a central database and made available for advanced searches and reports via a modern Web interface and the command line.
 htmLawed is a PHP script to process text with HTML markup to make it more compliant with HTML standards and administrative policies. It works by making HTML well-formed with balanced and properly nested tags, neutralizing code that may be used for cross-site scripting (XSS) attacks, allowing only specified HTML tags and attributes and URL protocols through black- or white-lists. It can also tidy/pretty-print HTML, make relative URLs absolute, check for spam, etc. It is small (single file of ~50
htmLawed is a PHP script to process text with HTML markup to make it more compliant with HTML standards and administrative policies. It works by making HTML well-formed with balanced and properly nested tags, neutralizing code that may be used for cross-site scripting (XSS) attacks, allowing only specified HTML tags and attributes and URL protocols through black- or white-lists. It can also tidy/pretty-print HTML, make relative URLs absolute, check for spam, etc. It is small (single file of ~50
 minimalist password safe with full-screen pager and password generation profiles
minimalist password safe with full-screen pager and password generation profiles
 The RedMatrix (aka "red") is an open source webapp providing a complete decentralised publishing, sharing, and communications system. It combines communications (private messaging, chat and social networking), and media management (photos, events, files, web pages, shareable apps) with enough features to make your head spin. What makes the RedMatrix unique is what we call "magic authentication" - which is based on our groundbreaking work in decentralised identity services. This ties all RedMa
The RedMatrix (aka "red") is an open source webapp providing a complete decentralised publishing, sharing, and communications system. It combines communications (private messaging, chat and social networking), and media management (photos, events, files, web pages, shareable apps) with enough features to make your head spin. What makes the RedMatrix unique is what we call "magic authentication" - which is based on our groundbreaking work in decentralised identity services. This ties all RedMa
 The OpenSSL Project is a collaborative effort to develop a robust, commercial-grade, fully featured, and Open Source toolkit implementing the Secure Sockets Layer (SSLv2/v3) and Transport Layer Security (TLSv1) as well as a full-strength general-purpose cryptography library.
The OpenSSL Project is a collaborative effort to develop a robust, commercial-grade, fully featured, and Open Source toolkit implementing the Secure Sockets Layer (SSLv2/v3) and Transport Layer Security (TLSv1) as well as a full-strength general-purpose cryptography library.
 The WiKID Strong Authentication System is a highly scalable, secure, self-hosted two-factor authentication system. It is simple to implement and maintain, allows users to be validated automatically, requires no hardware tokens, has a simple API for application support (via Ruby, PHP, Java, COM, Python, etc.), supports multiple domains, and supports replication. It also supports mutual/host authentication, wireless tokens only domains, locked tokens (to your PC), anti-keystroke logger keypad PIN
The WiKID Strong Authentication System is a highly scalable, secure, self-hosted two-factor authentication system. It is simple to implement and maintain, allows users to be validated automatically, requires no hardware tokens, has a simple API for application support (via Ruby, PHP, Java, COM, Python, etc.), supports multiple domains, and supports replication. It also supports mutual/host authentication, wireless tokens only domains, locked tokens (to your PC), anti-keystroke logger keypad PIN
 A Netfilter firewall tool written in bash scripting, designed to be easy to use but yet flexible and powerful.
A Netfilter firewall tool written in bash scripting, designed to be easy to use but yet flexible and powerful.
 bWAPP is an "extremely buggy wep app" intended for researching and discovering common security issues. It deliberately covers over 100 vulnerabilities ranging from SQL injection, to XSS, CGI exploits, SSL tampering, remote code execution, RFI, SSRF, CORS, buffer overflows; and replicates many high-profile exploits of other applications (Drupal, Wordpress). It's implemented in PHP, but of course only meant to be run in a sandbox or with its bee-box VM exposing further server process vulnerabili
bWAPP is an "extremely buggy wep app" intended for researching and discovering common security issues. It deliberately covers over 100 vulnerabilities ranging from SQL injection, to XSS, CGI exploits, SSL tampering, remote code execution, RFI, SSRF, CORS, buffer overflows; and replicates many high-profile exploits of other applications (Drupal, Wordpress). It's implemented in PHP, but of course only meant to be run in a sandbox or with its bee-box VM exposing further server process vulnerabili
 ArpON is a daemon that handles and inspects ARP (address resolution protcol) requests and thusly can prevent MITM attacks, ARP sppofing, cache or route poisoning. It also blocks related network attacks like ARP sniffing, hijacking, or injection, or higher-level DNS and HTTP request/session spoofing, or SSL/TLS circumvention. It also protects networks with proactive (network interface or system shutdown) and dynamic ARP traffic inspections in complexer setups.
ArpON is a daemon that handles and inspects ARP (address resolution protcol) requests and thusly can prevent MITM attacks, ARP sppofing, cache or route poisoning. It also blocks related network attacks like ARP sniffing, hijacking, or injection, or higher-level DNS and HTTP request/session spoofing, or SSL/TLS circumvention. It also protects networks with proactive (network interface or system shutdown) and dynamic ARP traffic inspections in complexer setups.
 mod_sslcrl is an Apache module for automating validation of SSL/TLS client certifcates against revocation lists (CRL). It's used in conjunction to mod_ssl when x509 client certificate authentication is used. It substitutes the directives SSLCARevocationFile and SSLCARevocationPath.
mod_sslcrl is an Apache module for automating validation of SSL/TLS client certifcates against revocation lists (CRL). It's used in conjunction to mod_ssl when x509 client certificate authentication is used. It substitutes the directives SSLCARevocationFile and SSLCARevocationPath.
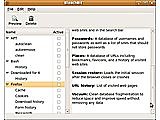 BleachBit is a privacy helper that erases unused disk space after cleaning up cache, cookies, internet history, temporary files, logs and junk data. It known where to look for browser and other common application data, often also speeding up those after vacuuming their data stores. Deletion is actually implemented as shredding with multiple overwrites.
BleachBit is a privacy helper that erases unused disk space after cleaning up cache, cookies, internet history, temporary files, logs and junk data. It known where to look for browser and other common application data, often also speeding up those after vacuuming their data stores. Deletion is actually implemented as shredding with multiple overwrites.
 PolarSSL is a light-weight cryptographic and SSL/TLS library written in C. PolarSSL makes it easy for developers to include cryptographic and SSL/TLS capabilities in their (embedded) applications with as little hassle as possible. Loose coupling of the components inside the library means that it is easy to separate the parts that are needed, without needing to include the total library. PolarSSL is written with embedded systems in mind and has been ported on a number of architectures, including
PolarSSL is a light-weight cryptographic and SSL/TLS library written in C. PolarSSL makes it easy for developers to include cryptographic and SSL/TLS capabilities in their (embedded) applications with as little hassle as possible. Loose coupling of the components inside the library means that it is easy to separate the parts that are needed, without needing to include the total library. PolarSSL is written with embedded systems in mind and has been ported on a number of architectures, including
|